A wise man once told me, the company of wise men makes one knowledgeable and wise. :-)
So it happens that with my colleague Thiery being around in office I’m getting some IT-Sec best practices too. I was always too lazy to set-up SSH authentication via keys … and I would continue typing my root password every time. Then last Friday Thiery decided with some brainwashing, taking example the recent cyber-attack in South Korea.
To get things done here are the steps; best explained through screenshot.
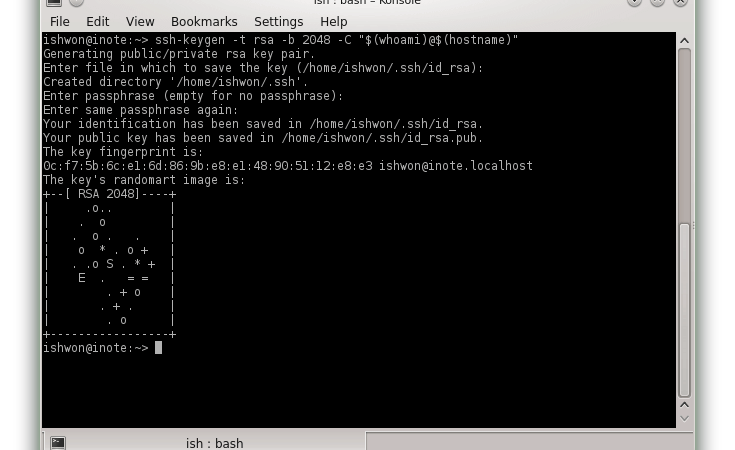
Once the key generated copy it to the remote server.
ssh-copy-id username@remote-server.org
If you have entered a passphrase in the step above you will need to provide that at every ssh session. An ssh agent will cache the decrypted keys and thus latter sessions will not prompt for passphrase. The default with openSSH is ssh-agent. I’m using Keychain which is a tiny program that manages the ssh-agent perfectly.
Just install the keychain program (it’s surely available in the repos) and append the following line in ~/.bash_profile.
eval $(keychain --eval --agents ssh -Q --quiet id_ecdsa)