Spyware: Flashlight application on Smartphones
November 11, 2014
 I came across this video stating a “confirmed” incidence of spyware on around 500 million smartphones. The person intervening in the video stated that popular Flashlight applications were collecting information on mobile devices and send over the Internet.
I came across this video stating a “confirmed” incidence of spyware on around 500 million smartphones. The person intervening in the video stated that popular Flashlight applications were collecting information on mobile devices and send over the Internet.
I do have a Flashlight app too & I instantly checked its usage. Indeed, it is a whopping 11.60MB on disk (assuming it has to only switch ON & OFF the led).
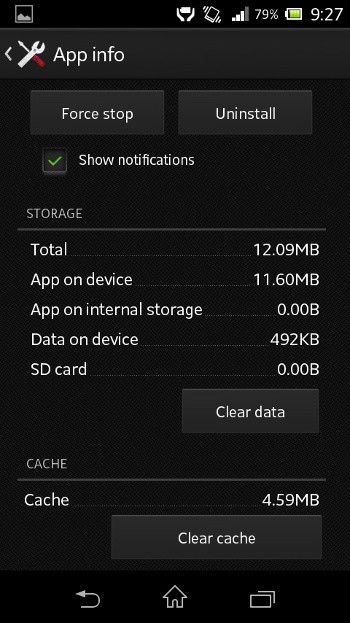
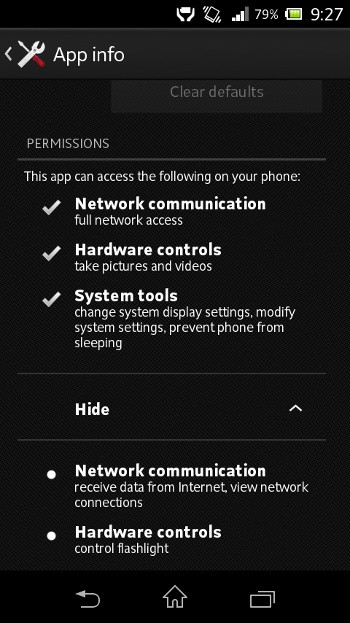
I checked its permissions and the app has network access rights. Now, that sounds fishy for an app that is supposed to only switch ON & OFF the led device.
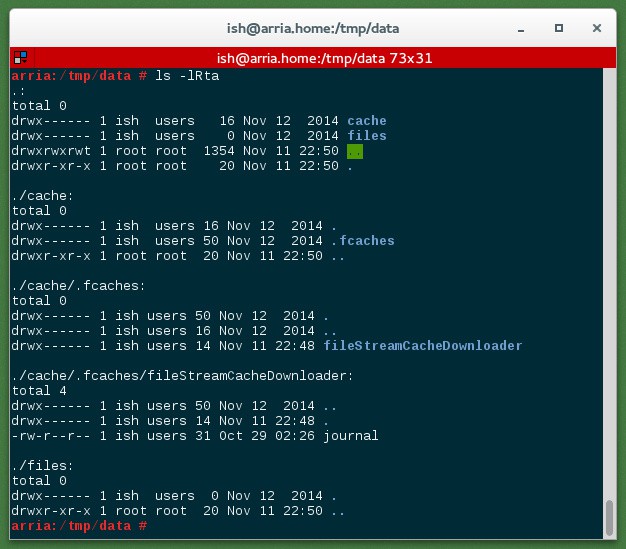
The application has a data folder. I transferred it to my laptop for further analysis. The hierarchy broke down to the following:
The application permissions level are as follows:
- Required to be able to access the camera device
- Allows access to the flashlight
- Allows an application to modify the current configuration, such as locale
- Allows an application to read or write the system settings
- Allows using PowerManager WakeLocks to keep processor from sleeping or screen from dimming
- Allows applications to access information about networks
- Allows applications to open network sockets
- Allows read only access to phone state
- Allows an application to get information about the currently or recently running tasks
- Allows an application to write to external storage
- Allows applications to access information about Wi-Fi networks
- Allows an application to use C2DM (Cloud to Device Messaging) service
So, they collect the IP address? A Flashlight application that needs to collect the IP address. Dring! Dring! Gets interesting. Let’s see ahead.How we use your information we collect
1. Personal Information. We do NOT collect and use Personal Information in any way. 2. Non-personal Information. Generally non-personal information is used internally to monitor and improve the Services, to perform analyses of the behavior of our users, to measure user demographics and interests, to describe our services to third parties such as advertisers and to analyze how and where best to use our resources. We do not combine Non-Personal Information with Personal Information.How we share the information we collect
1. Personal Information. We do NOT collect and share Personal Information in any way. 2. Non-personal information. We accept advertisements from Third Parties ad networks which may be displayed in our Apps. We may share certain information with third-party advertisers, ad networks and ad platforms (“Advertising Entities”) to develop and deliver targeted advertising in the Apps. We may also allow Advertising Entities to collect non-personal information within the Services which they may share with us, including your device identifier, device type, device brand, device model, network type, device language, and IP address. Advertising entities may also collect non-personal information related to the performance of the advertisements, such as how many times an advertisement is shown, how long an advertisement is viewed, and any click-throughs of an advertisement.
The privacy policy continues as follows:
In short, they will reveal my IP address under legal obligation. Just to remind, Super-Bright LED Flashlight’s page on Google Play Store says 500 million installs. Basically, they have a data bank of 500 million Internet capable devices.Compliance with laws and law enforcement
Surpax reserves the right to share your information with third parties if we believe such action is necessary in order to: (1) conform with the requirements of the law or to comply with legal process served upon us; (2) protect or defend our legal rights or property (3) investigate, prevent or take action regarding illegal activities, suspected fraud, situations involving potential threats to the physical safety of any person or violations of the terms and conditions of using our Apps and Services.
On that note, it’s time to learn Mobile Application Development & I code my own Flashlight application rather than trusting off-the-shelf. All of a sudden I feel Richard Stallman was right.
Why don’t you use a cell phone?Because cell phones can track my location or my conversation with anyone. Most cellular phones, even if they are not smartphones, do have a processor running software and that (proprietary) software is malware, because it will send information about its users’ locations on remote command — and it has a back-door, so it can be remotely converted into a listening device. Almost all software has bugs — but this software is itself a bug.
Source: opensourceforu.com
Update - 12 Nov 2014, 07h07
A good fellow, Anwar, from the Mauritius Internet Users Group shared an article from SnoopWall pertaining to intrusive Flashlight applications.
For an Ad-Free privacy hardened Flashlight, one could use Privacy Flashlight by SnoopWall.