Shellshock: A survival guide
October 25, 2014
It’s been the hot talk since a few weeks. Well, the presentation was finally due today at the University of Mauritius. Scheduled for 13h00, however I reached at noon. Planned to meet Shelly first and explain her a little about Linux (in general) and then show her what’s Bash. In a few quick lines, that happened to be Bash 101.
As I got down from the bus, I pinged Om, then Shelly, and Saamiyah. One was having lunch at Ken’s, the other waiting for me at the cafeteria and the latter getting down from the bus too. Saamiyah went to meet other UoM CC folks who were apparently having a “meeting”, some sort of “handing over”. In my mind that sounded like something official. I said I would join them later; let me quickly grab something to eat and get on with a Bash 101 for Shelly.
She awed at the cool tricks that usually make people smile. Yup! Those were the little goodies with « cowsay » and « sl » …
A while later JoKi called, he reached too, along with the kids. Told him we’re having lunch and let us meet at the cafeteria itself before going to the Prez room. A few others called, with the mob ringing every 3 - 5 minutes; I kinda felt like a LUGM secretary. Am I? Nope! I’m not.
We then went to meet UoM Computer Club folks. Oh! Their “handing over” was more party-like (^^,) … instead of some boring/official thing.

Spent a moment with them while they were cheering for “I could not figure why” … It was 13h00 and by that time Logan reached cafeteria, I was told. I asked folks to move to Room 1.16 where the prez was scheduled, not to be late. Alas! The room was taken up by others. The one next to it, room 1.14 was free though, so we took that instead.
Slowly, the room filled up. As Logan was busy setting up the projector & testing the gear, JoKi gave a brief intro about the user groups, what we do and how students could benefit from it. I then tossed S. Moonesamy (SM as we call him) to introduce MIU (Mauritius Internet Users) group. He instead asked me to do it & he only joined in to add a couple of stuffs that I missed.

A while later Ajay reached. We were just waiting for him to bring his camcorder. Hopefully if the recording has been ok, we should have the Shellshock Prez on LUGM’s Youtube Channel.
Then Logan took over. He introduced himself, told us about his work and contributions in open source. He went through a couple of projects explaining what they do etc; especially for those who were new. The presentation was focused on Bash; however Logan quickly named a few other shells and highlighted security features of Korn Shell (the default shell in the BSD family).

Before Logan comes on the Shellshock part, he showed how a variable is declared in Bash and how it is expected to be interpreted. Then he showed an example of code that could be inserted in the Bash environment and it would be executed. Followed next was a series of questions from the audience, each trying to understand how this could cause potential damage to a system. On my end I was more interested to know about permission restrictions. Ajay pitched in with his explanation; which were helpful indeed.
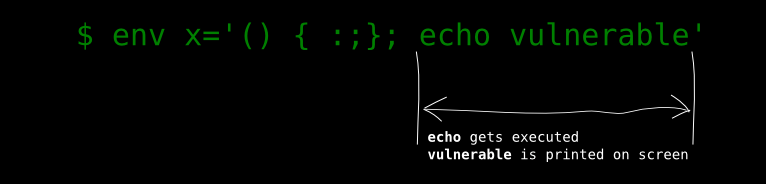
We usually use single quotes when declaring variables in Bash; especially when we have to store a string of characters. These characters should be treated as texts and not commands. For example if our string of characters contains a word like who then it should treat it as a simple text rather than executing the who command.

In the above example, who will be printed on the screen and not executed.
However, with a Shellshock un-patched Bash, one could send a couple of braces & semi-colon and this time who gets executed. For the sake of convenience in our example, let’s use the word echo followed by vulnerable.
Logan mentioned two patches that have been proposed so far. One is a BSD contributed patch which is hardened, however it could potentially break existing scripts. In a scenario involving thousands of servers with hundreds of thousands of scripts to be modified, the hardened patch doesn’t sound practical. Thus to mitigate the same, Logan proposed a solution similar to the FreeBSD Jail. Linux alternatives to the FreeBSD Jail are LXC, OpenVZ, Docker among others. Thus, one could apply a system-wide “soft” patch and isolate a publicly accessible application with a hardened patch. The only scripts to be modified will be those required by the “public application”.


Presentation ended with an interactive Q&A session. At that moment, I was having a chat with Nirvan outside the room. So, I kinda missed a couple of questions.
Afterward we went back to the cafeteria, had coffee, roti and triggered some geek chat. While I still had to finish my coffee it was announced that cafeteria would close in 5 mins. Aaargh! We thus settled for a tree-meetup; that’s usually the bench under the tree at University of Mauritius Cafe & Auditorium area.

