Sharepoint misconfiguration, yet again
October 5, 2014
In my previous articles where I related my observation on the Government of Mauritius Web Portal’s Sharepoint misconfiguration, I mentioned that the Sharepoint product is a robust one but also configuration is meticulous. One has to pay particular attention to the global config file, otherwise unintended data leakage could happen.
In the case of the Mauritian Gov Portal, I was able to get access to the Sharepoint Admin panel with just some URL short-cut and a normal user account.
Recently, while still trying to improve my knowledge in Sharepoint configs, I came across another website having a misconfiguration. That was of the US Naval Sea Systems Command. In the beginning I wasn’t sure if the documents were really intended to be online. However, one thing I was sure of, the interface through which the documents are coming online isn’t proper. All documents that are targeted at an online audience should be made available through custom-designed pages, giving access to specific files.
Sharepoint has a virtual directory in IIS (web server) called _layouts. This directory usually holds pages that enable to view & manage content. Direct access to this folder should be disabled and certainly public access is not recommended. Search engine indexing of this folder’s content is also discouraged.
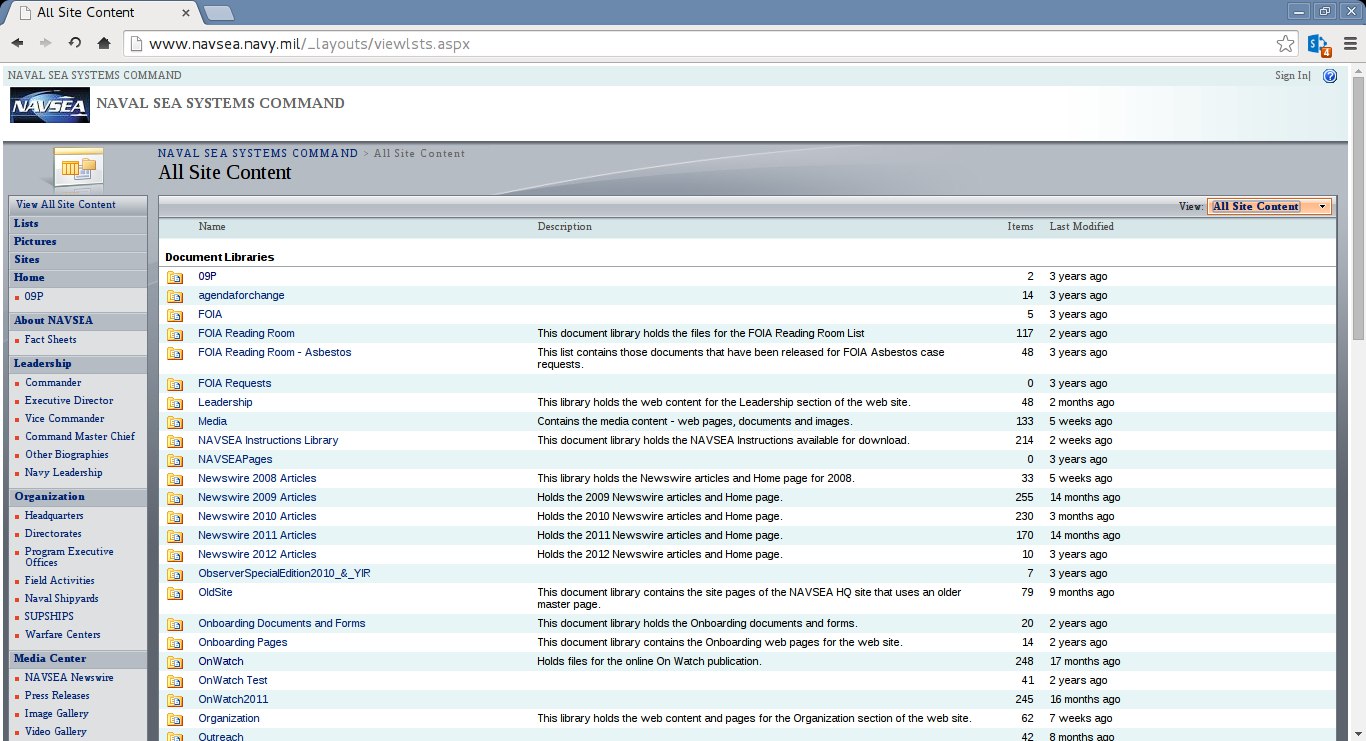
While observing the NAVSEA website, direct access to _layouts was denied since Gobal Directory Listing was disabled. However, anonymous/public access to individual pages remained enabled. Due to this configuration, anybody could simply call the viewlsts.aspx page and access all the files & folders available for the Sharepoint Web Framework.
Thus, the link http://www.navsea.navy.mil/_layouts/viewlsts.aspx lead to the following:
While a lot of the content are intended for public viewing, this page itself should not have been given public access. Various sections contain instructions on how to use the framework and instructions on publishing content.
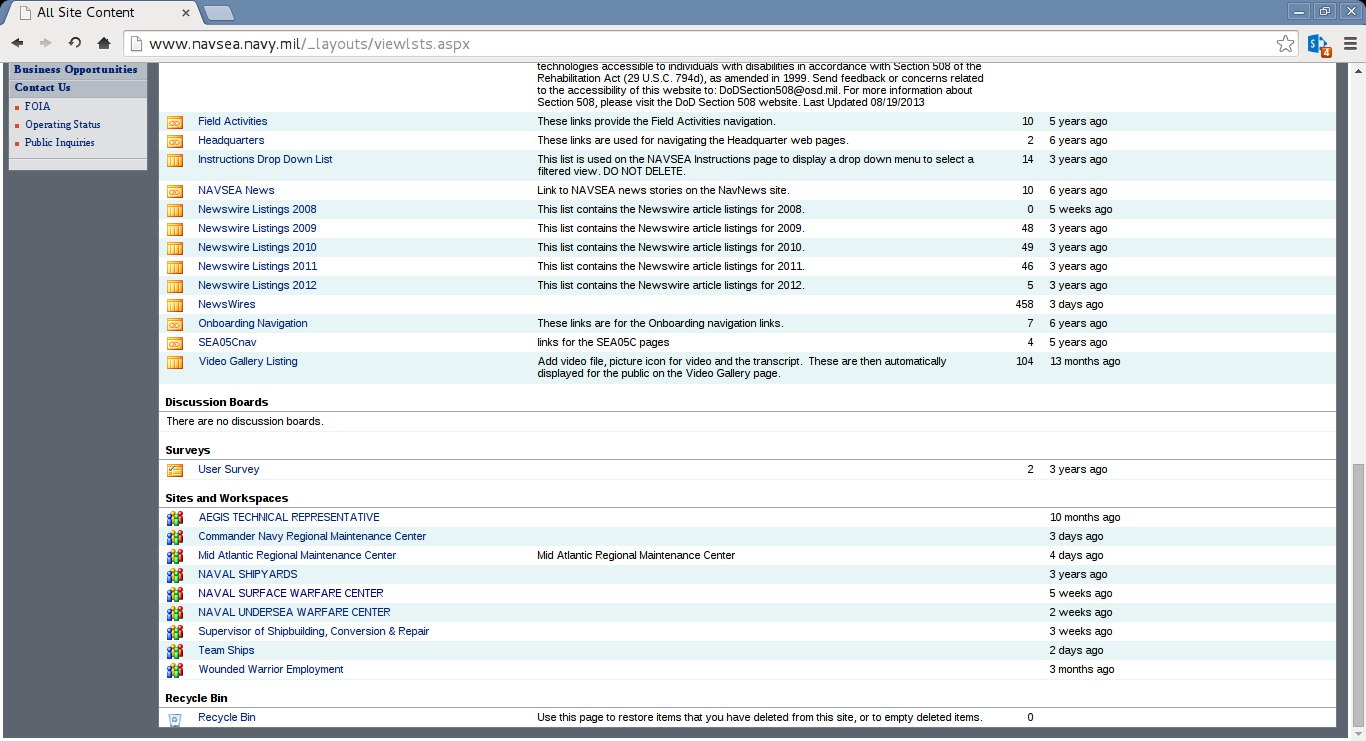
These are internal instructions. Many folders have “short names” which surely are interpreted by internal staff only.
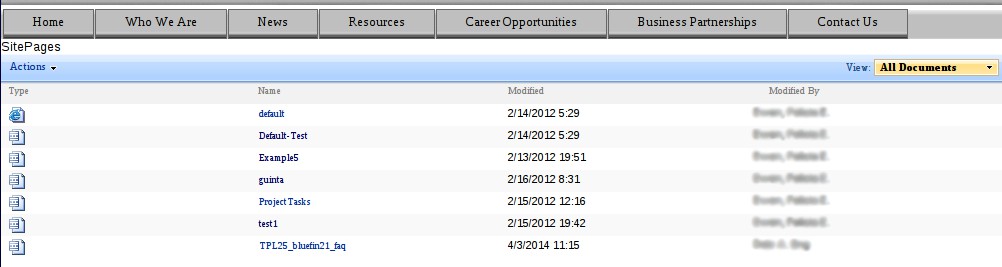
Another example is the “SitePages” folder that gives way to test pages that again are supposed to be visible only to internal staff and not accessible by public from the Internet.
Well, to conclude, the Sharepoint of US Naval Sea Systems Command does have a Sharepoint misconfiguration that could potentially allow data leakage.
The privacy policy of the website clearly states that content on the website is intended for public access. It also warns against unauthorized attempts at uploading or changing information on the website, which may be punishable under the Computer Fraud and Abuse Act of 1986 and the National Information Infrastructure Protection Act.
However, my argument still stands valid, the content could be for public view but they should be accessible via a custom page and not giving full public view to all the web content including test pages and internal instructions.
In the website’s footer, I could find the webmaster’s email address. I thus emailed the person regarding this observation.
All observation carried out on the NAVSEA website are naked eye without any Forensic / Web Penetration testing tool. I can't say if vulnerabilities exist in this web application. My observation limits me only to information that is publicly accessible and I comment on their nature. The viewlsts.aspx page of NAVSEA appears on search engine results and that's where I got a hint of a possible Sharepoint misconfiguration. All screenshots have been taken from NAVSEA website.
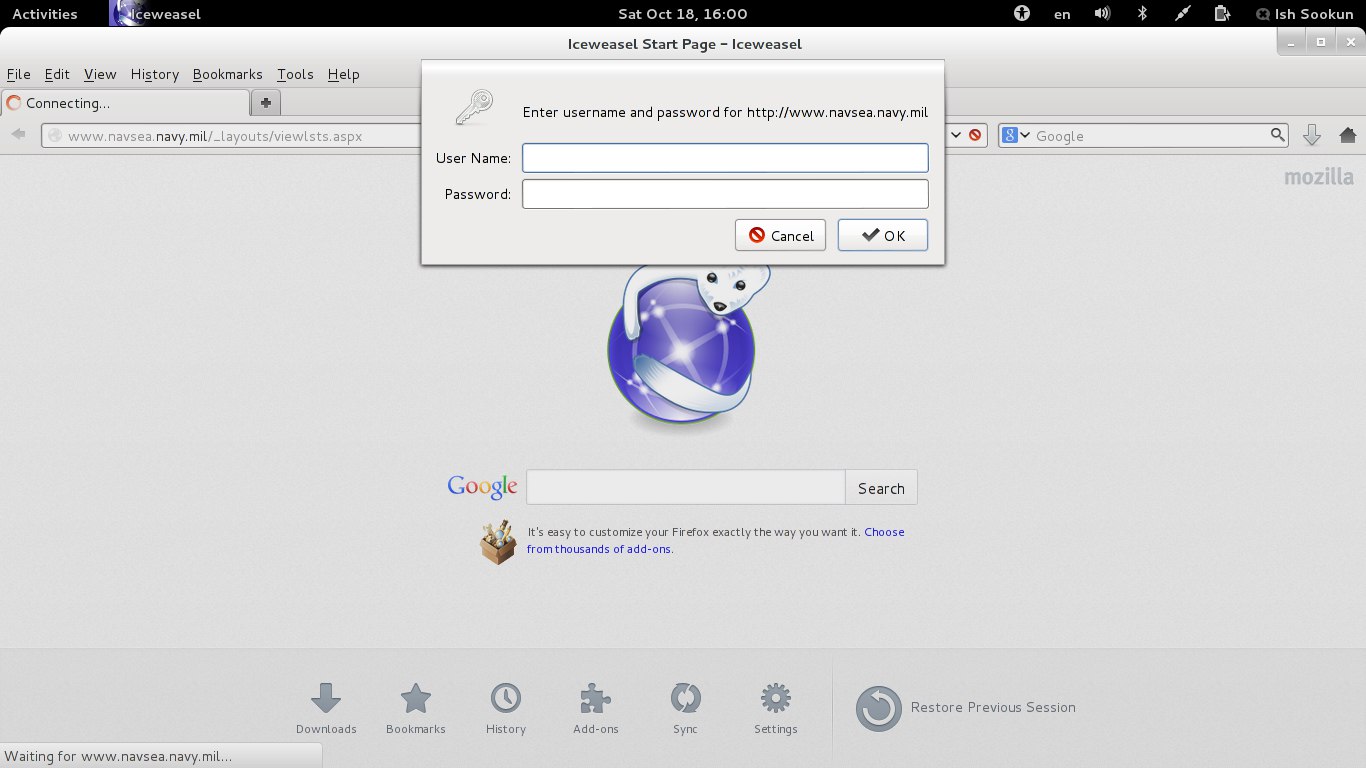
Update - 18 Oct 2014 / 16h00
While checking the page today, I found that access has been restricted now. Courtesy would suggest they replied me at least but never mind, I’m kind of used to Government-Ego stuffs.