OpenSSL: More vulnerabilities, CVE-2014-0224
June 8, 2014
Earlier today, Logan, posted on the LUGM facebook group that he has created a online tool (still in beta) that would test if your server is vulnerable to yet another vulnerability that has been recently discovered in OpenSSL. This particular vulnerability is known as CVE-2014-0224.
For Internet users in general let’s see what is a CVE. It’s a short form for Common Vulnerabilities and Exposures. MITRE Corporation maintains a list of these vulnerabilities and they are tagged with CVE identifiers in the following format:
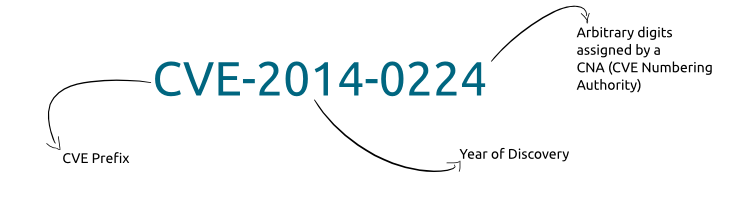
Mitre Corporation describes the vulnerability as follows:
OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h does not properly restrict processing of ChangeCipherSpec messages, which allows man-in-the-middle attackers to trigger use of a zero-length master key in certain OpenSSL-to-OpenSSL communications, and consequently hijack sessions or obtain sensitive information, via a crafted TLS handshake, aka the “CCS Injection” vulnerability.
A quick chat with Logan & he confirmed me that the current Injection Tester by NCC Group is not reliable. He tried to contact the author but to no avail. Finally, he decided to write a tool. He coded the back-end and S. Moonesamy (SM as we call him) wrote the front-end. SM also provided hosting for the tool, through his company Elandsys.
The SSL Injection Test is available here.
I tested a few websites which I’ve worked on, all good, while some other local websites not good at all.
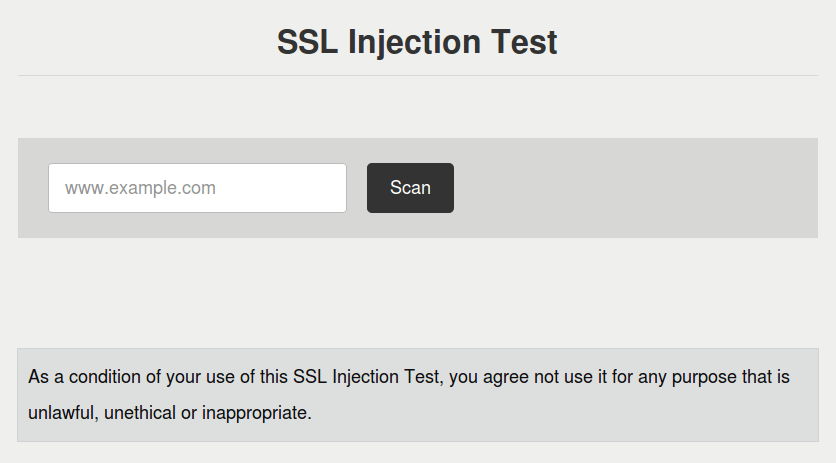
If you find your server as vulnerable & you require expertise to patch it, you may contact S. Moonesamy. He’s a good old fellow who has been contributing in the industry & worked closely on the security aspects of Internet.
Logan has alerted Google, Yahoo, Youtube and Ebay.
I sent an email to CERT-MU (Mauritian National Computer Security Incident Response Team) notifying them of the same.
I should also highlight that OpenBSD developers including Logan, are currently fine-tuning LibreSSL (an OpenSSL fork) and many security fixes have been brought including CVE-2014-0224 being patched. Please support the good work of these fellows by donating to the project.