MTPA leaks 269,146 email addresses
October 13, 2014
« ti problem » isn’t something new in our country!
Latest to join the crew (breaching privacy) is the Mauritius Tourism Promotion Authority (MTPA). It all started with an email that S. Moonesamy (SM) sent on the MIU discussion list.
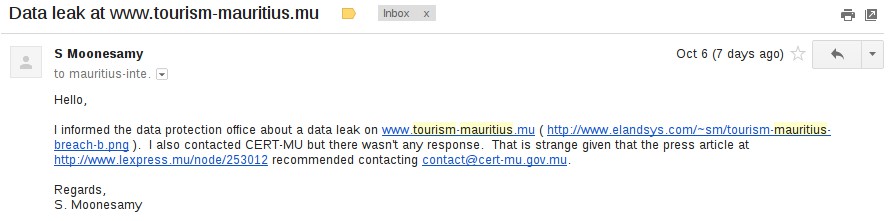
The screenshot that SM referred to can be accessed here. It’s been a week since SM sent that email and I guessed things must have been solved by now. So, I went for a troll on the MTPA website.
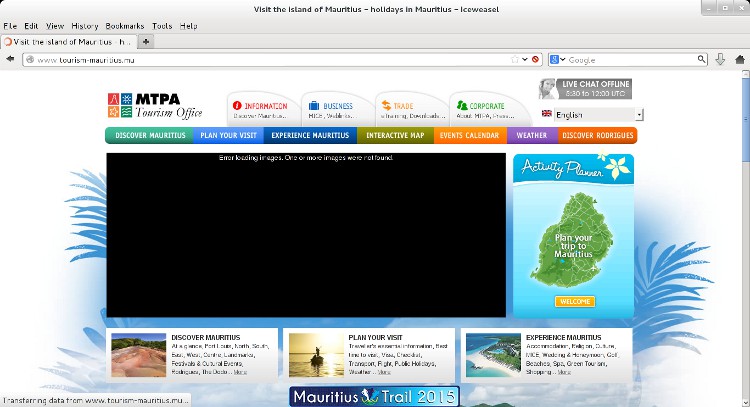
Oops! It’s disastrous. Let’s see why…
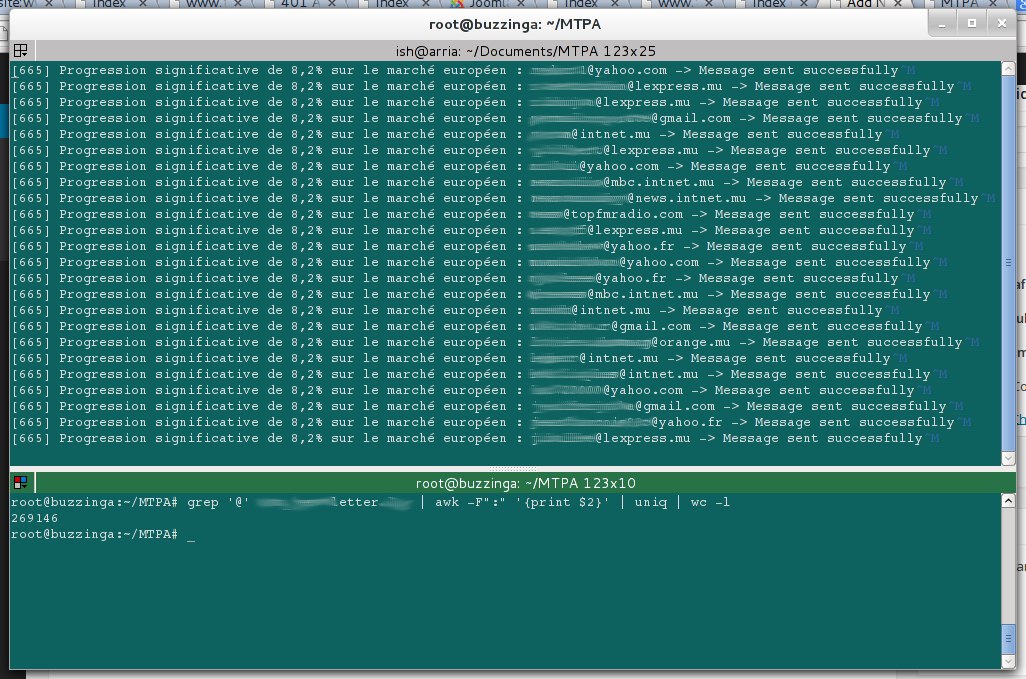
The server hosting MTPA website allows public access to all its directories, thus letting « sensitive data » leaking through. Among those is a 56MB log file that contains transactions of all newsletters sent out from 8 June 2011 till 10 October 2014. The file contains 269,146 email addresses (excluding multiple entries) ranging from individuals to government officers, as well as journalists.
That would be a gold mine for spammers seeking email addresses. Well, as if such a privacy breach was not enough. I stumbled across two more files that gave me a (/_-) #facepalm
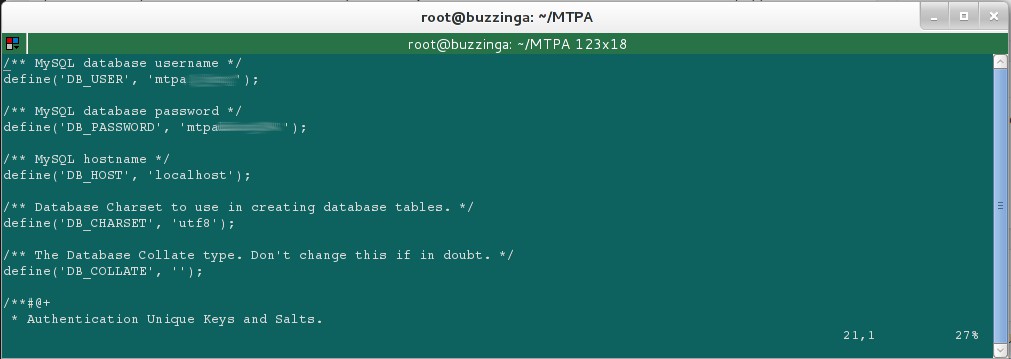
Those files contain the username & password for the MTPA website and blog.
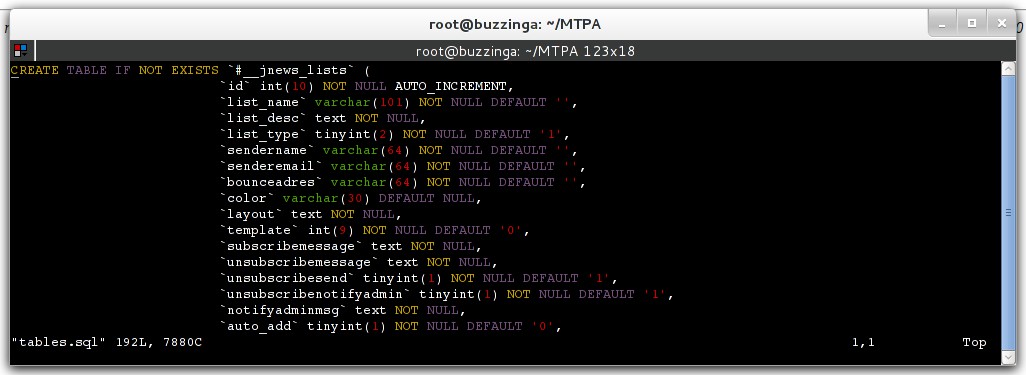
Finally, how about the original setup SQL files that are still wandering around? Could they be dangerous?
Now, as we can see, in the original mail SM contacted CERT-MU alerting them of the issue. Clearly the website of the Mauritius Tourism Promotion Authority is vulnerable. Such vulnerabilities, especially where data is leaked, could be directed to CERT-MU. Oh! For those who don’t know, CERT-MU is the Mauritian National Computer Security Incident Response Team. However, they are famous for not replying emails. So, no wonder why even after a week SM didn’t receive a reply. On my end, I’m sending them another email with the hope they wake up.
This blog post is based on naked eye observation pertaining to elements that are publicly available from the MTPA website. At no moment any Web Penetration Testing Tool was used. Should anybody have query/doubts regarding this analysis, ping me.
Update #1 - 14 Oct 2014 / 18h37
Le Défi published the same after contacting both MTPA & me. MTPA confirmed the issue has been fixed. False!
I wasn’t contacted by the MTPA neither by CERT-MU. At the moment it looks like they didn’t identify the problem.