MNIC website's database still exploitable
May 21, 2014
L’Express article created a buzz over the privacy issue I published on my blog last week. Their article “technically” dubbed me as “hacker” which is inappropriate in the general sense and the use of words like “…il se targue…”, definitely doesn’t depict me. I wasn’t boasting about any exploit but rather amused & angry over the fact that how could a government website be so improper and poorly coded at it’s very core.
Hours after the whistle-blow of the unsecured Google Docs form on mnic.mu, it was taken down. So far, it was good, but other issues still lurk on the website. I also wrote about the poor code quality in a previous article. It garnered much attention & criticism from the community of IT Professionals. While the common user might not have understood the discussions over code quality, I might show you something more appropriate to a general audience.
On the MNIC website there is a search box on the top-right corner. Can you spot it? Good! Your first reflex usually is if you can’t find some information on the published pages, you will search it using that search box.
Now, let’s search for something like mnis. See below image for the result.
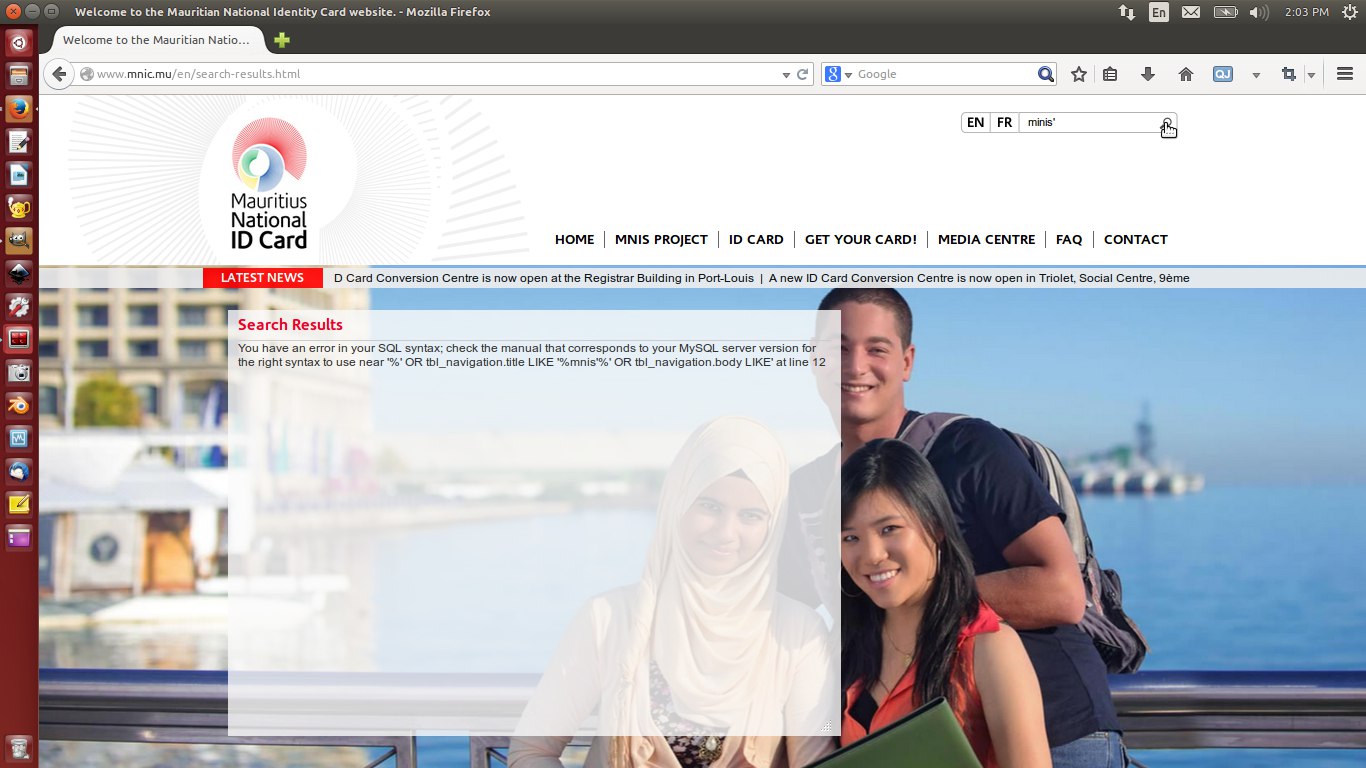
Looks fine. Right? Now, what if someone types mnis but since that person’s single-quote button is next to the Enter key just like on my keyboard, and the person accidentally hits the single-quote before hitting enter? See what happens.
What the babana is that? To the common user, it’s just a bunch of errors. However, to someone with malicious intentions this could be the key to the golden gate. Let’s have a closer look at the errors.
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '%' OR tbl_navigation.title LIKE '%mnis'%' OR tbl_navigation.body LIKE' at line 12
The errors printed above reveal table names from the MySQL database that should not have been shown at any cost. This mere error shows a blueprint of the website’s security. A person with enough of SQL kung-fu can retrieve data from the database or insert data into the database by exploiting this security loophole.
Why I published these?
Now some might argue why I am publishing these, if they are vulnerabilities shouldn’t I inform the authorities? Well, if you read my first article about the MNIC website, you’ll notice what I’ve published so far aren’t vulnerabilities invisible to the naked eye. They clearly are improper design & bad code at the very core of the website. I cast doubts over the handling of this website project, I don’t know how much it cost & I have doubts over those too, I doubt the supervision of the project, the security audits and finally doubts over awarding this project to whoever got it.