How to protect your phone from Stagefright?
October 12, 2015
A few weeks ago, Logan and some fellow geeks had a video podcast about Stagefright; the much feared Android vulnerabilities. News articles around the web have dubbed Stagefright as having the possibility to compromise millions of Android powered handsets. In fact, at the time of writing this blog post many mobile phone manufacturers haven’t yet released updates to fix Stagefright and other reported bugs.
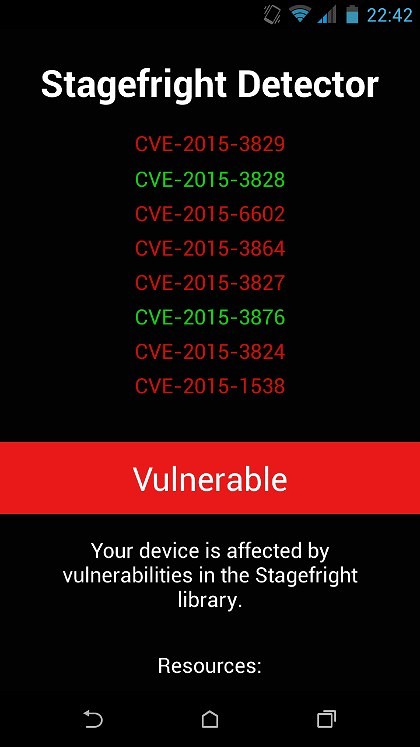
The Stagefright vulnerability was detected and reported by Joshua Drake, the VP of Platform Research and Exploitation and an expert at Zimperium zLabs. To verify if a mobile phone is vulnerable to Stagefright, one may use the Stagefright Detector app by Zimperium INC.
What is Stagefright?
Stagefright is a group of ‘bugs’ that have been identified and are potentially exploitable in the Android operating system. More information about these vulnerabilities are published under the following CVEs at cve.mitre.org:
CVE-2015-1538 CVE-2015-1539 CVE-2015-3824 CVE-2015-3826 CVE-2015-3827 CVE-2015-3828 CVE-2015-3829 CVE-2015-3864
How does Stagefright work?
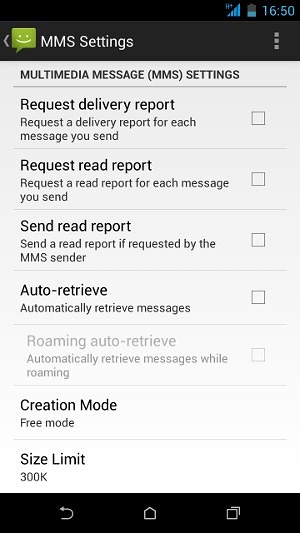
The attack happens by exploiting vulnerabilities in the Multimedia Messaging Service (MMS). An attacker can include a piece of malicious code in a video and send the same through MMS. Most handsets have the “auto-retrieve” feature enabled. Therefore, the code gets executed on the phone even if the phone’s owner does not open the message. This happens during the auto-retrieval of the message.
Depending on what sort of code is run, an attacker may get the ability to control the phone, execute commands, copy/delete files, trigger the camera at will etc.
How to protect your phone from Stagefright?
The best protection would come through security patches released by the phone manufacturer. Alas, until that happens, one is left with a vulnerable phone. Therefore, to mitigate a Stagefright attack, one could disable the “auto-retrieve” feature. To do so, navigate to:
Messages > Settings > Multimedia Message (MMS)
Thereby, disable the “auto-retrieve” feature.
However, this will only “mitigate” the attack. The malicious code does not get executed through auto-retrieval, but it will execute if the message is opened by someone.
To enforce an added security, one may disable the MMS functionality since it is not much a messaging tool used nowadays. To do so, go to:
Settings > Wireless & Networks > More > Mobile Networks > Access Point Names
You should normally find two APNs, one for SMS and one for MMS. I am subscribed to Orange Mauritius and the MMS APN is listed as “MMS Orange”. Once you have identified the correct APN, tap it and scroll down to the “APN enable/disable” option. That’s it. You may disable the MMS APN which will prevent your phone from both sending and receiving MMS.