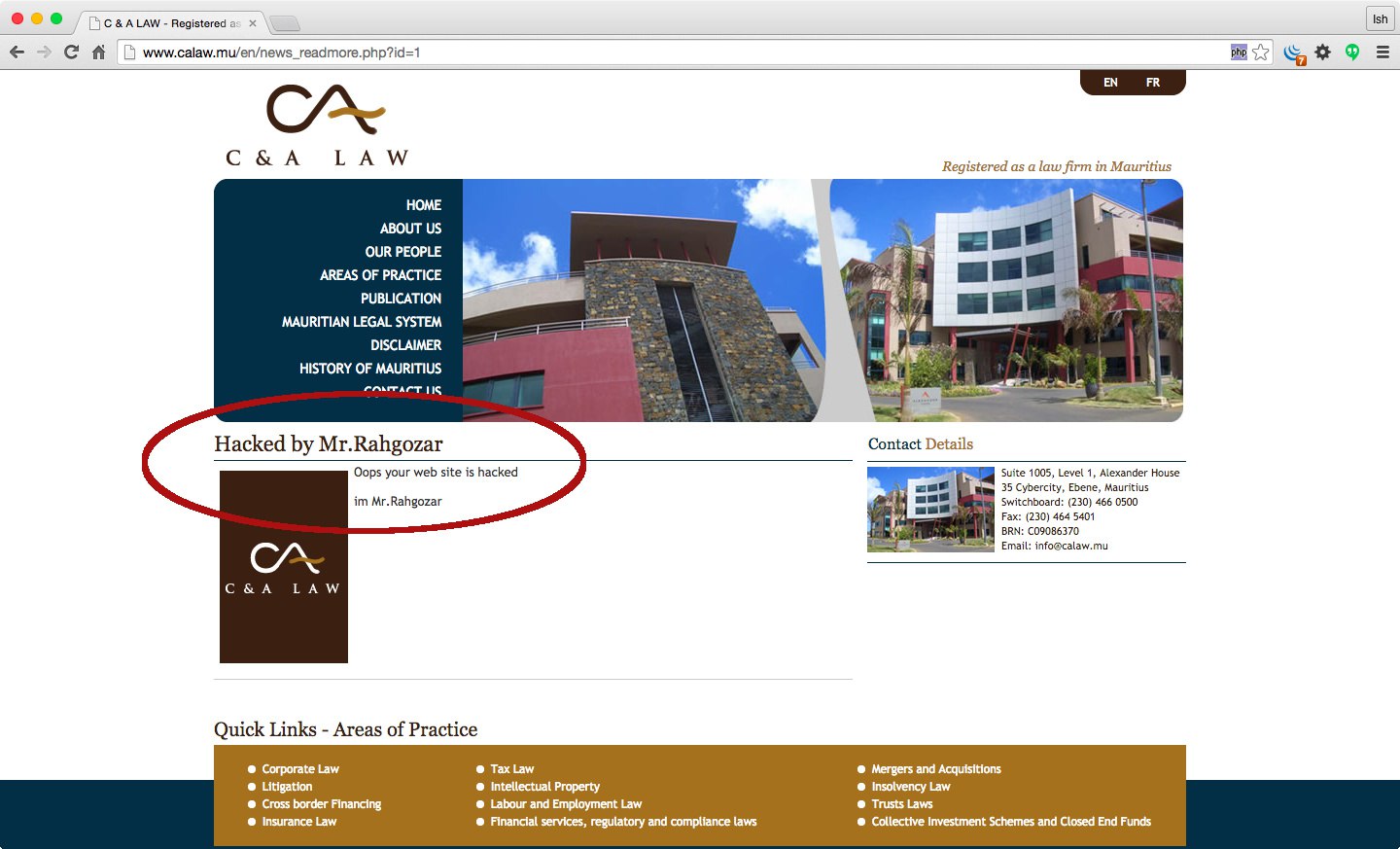
Hacked? Don't call CERT-MU.
February 2, 2015
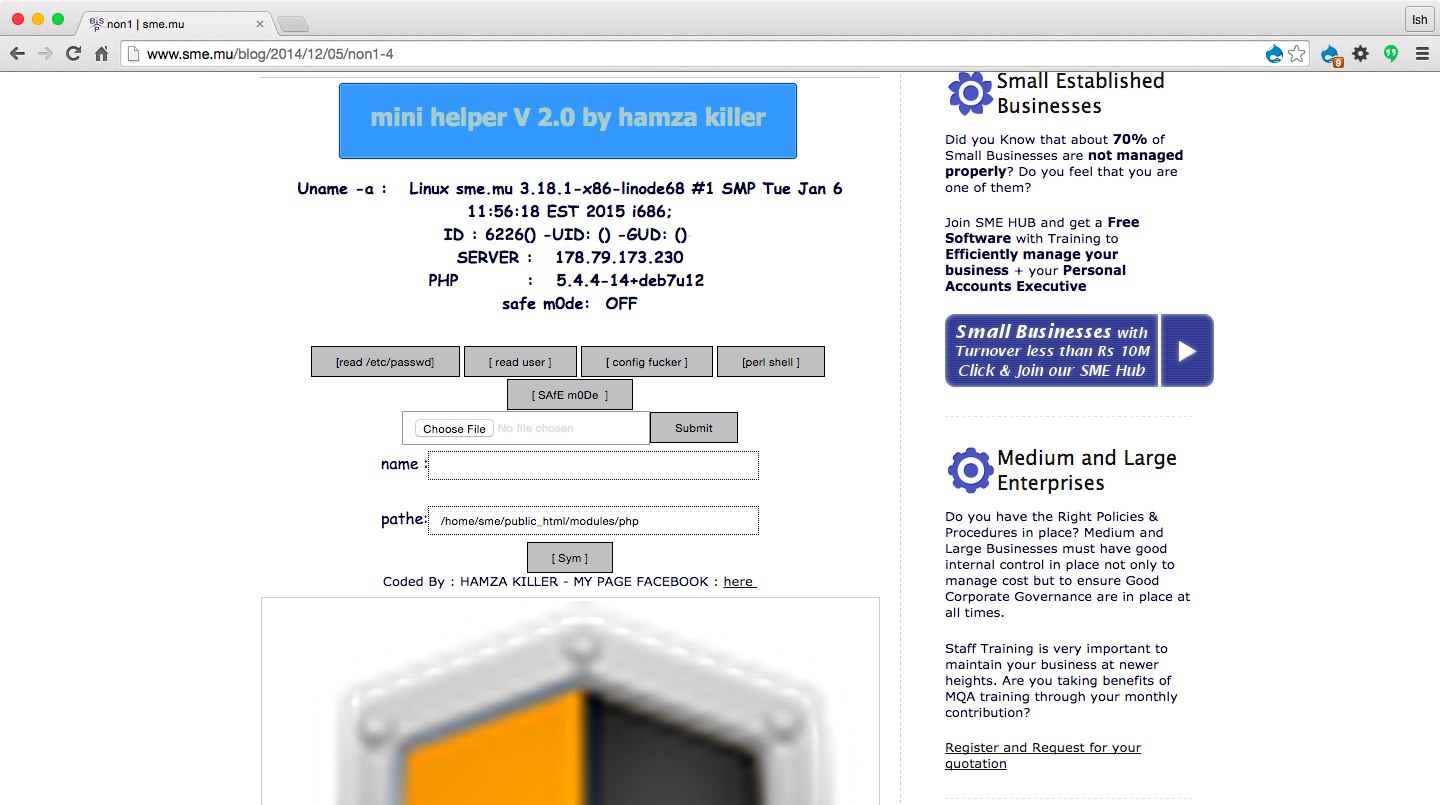
Few days ago, in the Mauritius Internet Users mailing list, it was tossed that something was wrong with the website sme.mu. I had a quick look and yes, the Drupal CMS was exploited to inject malicious code. Somebody trolled the webmaster and injected a tool dubbed as mini helper V 2.0.
I could not find the webmaster’s contact details on the website. Therefore I sent an email to CERT-MU alerting them of the situation. The server could be messed up by executing commands and upload more of the malicious scripts. I will not go into the details of how it was done as it’s not the scope of this article.
I alerted CERT-MU hoping they will respond in a transparent manner. However, it wasn’t the case. I did not receive any reply from CERT-MU and a few days later the webpage was cleaned up. The webpage seemed to be compromised since as early as November 2014 yet it went un-detected. While someone decides to trigger the alarm, there isn’t even an acknowledgement of receipt of mail. Maybe some times I ask too much!
Well, looks like alerting CERT-MU is futile. Transparency? Duh! So, folks, there have been much more attacks on local websites that have gone undetected for a long long time. Thank you CERT-MU for watching over us.
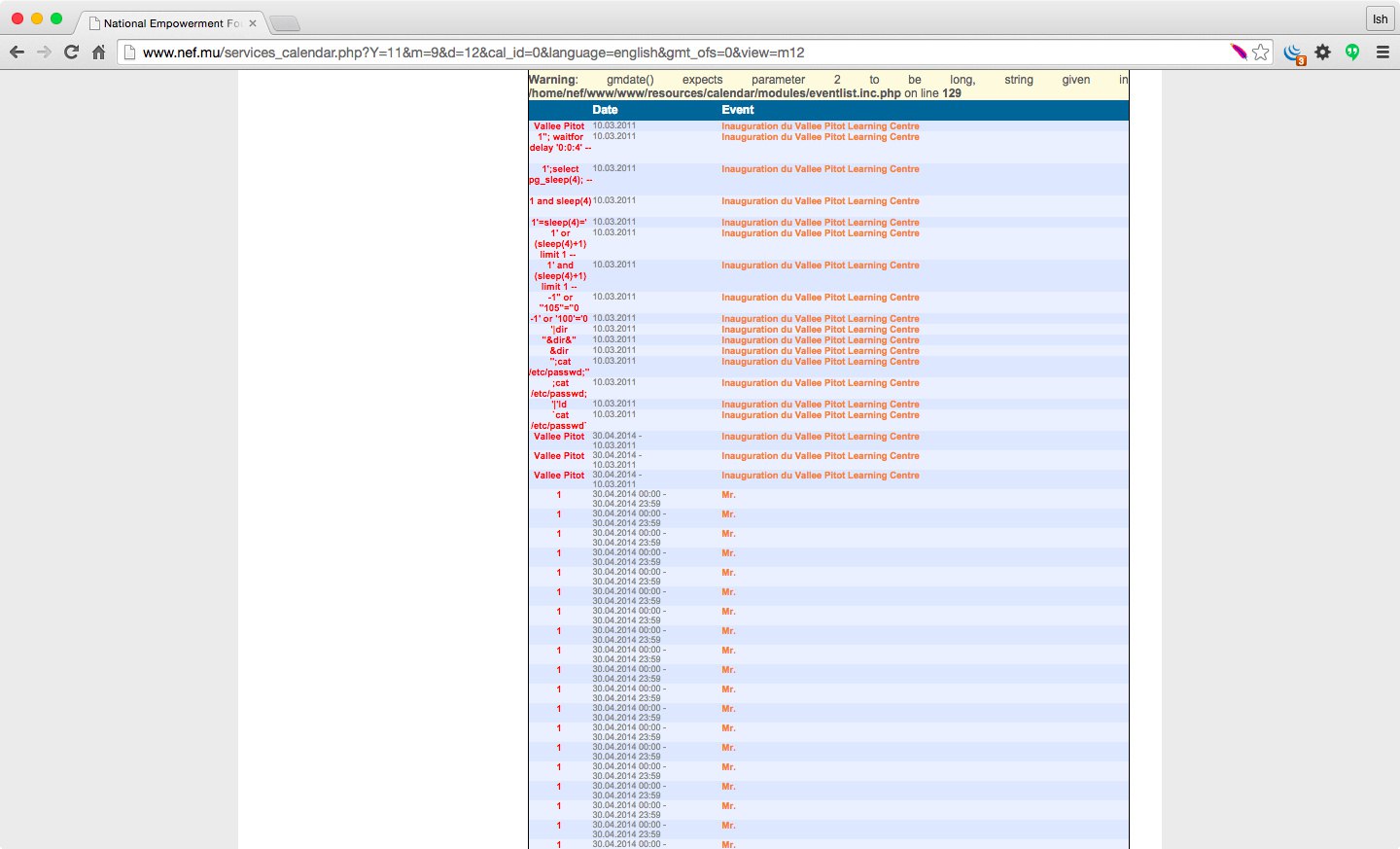
As at the moment, the National Empowerment Foundation website seems to have been successfully bugged by someone.
I recall somebody asking the CERT-MU’s officer-in-charge about incentives for people to report incidents, during the previous Cyber Security Conference by the National Computer Board. The response received was not encouraging.
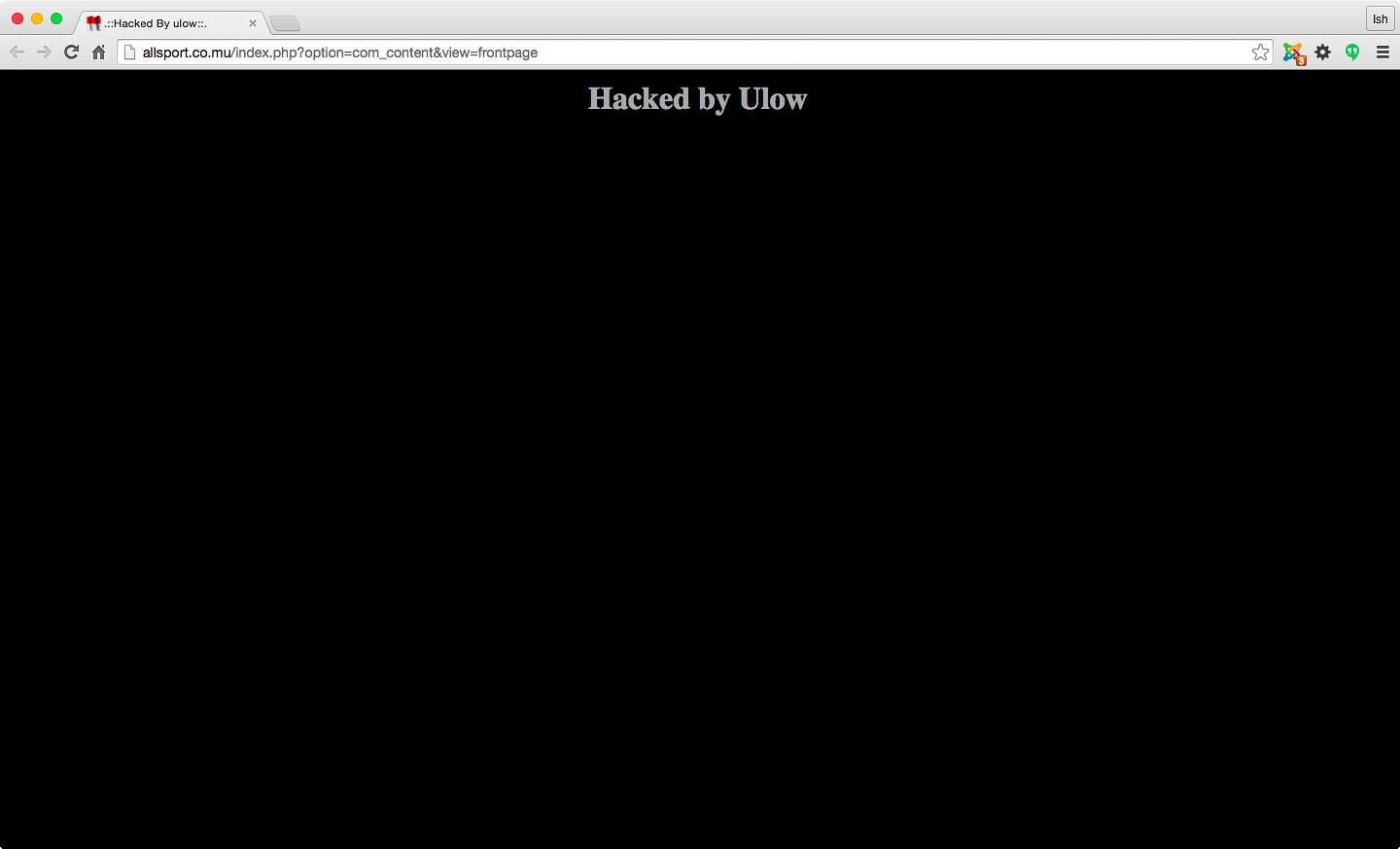
Now, if you’re wondering about the state of local “hacked” websites, you may have a look at the following defaced pages: