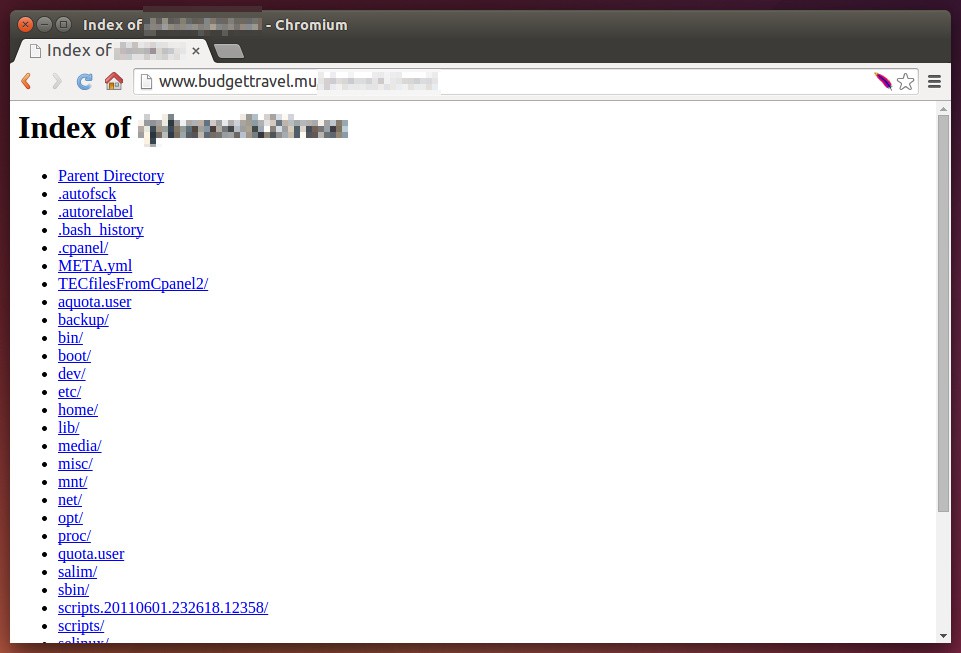
I visited a website today which is rugged with misconfigurations. My attention was caught by a list of Linux binaries & files that were accessible through the browser. One could see the list of user accounts on the machine through the famous passwd file, read the webserver’s (httpd) access log, view configuration files etc. Well, anyone with a little bit of Linux skills could find his way through.
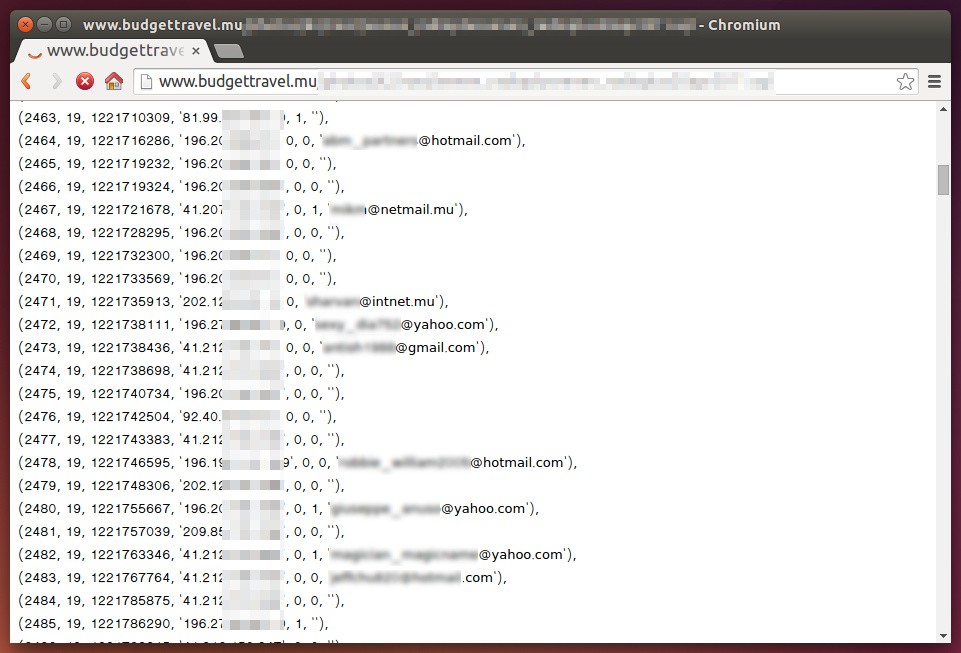
On a more serious note this particular website also happens to reveal an SQL file containing tons of IP adresses alongwith email addresses.
Based on what I could see above, I would flag this as both a security flaw and privacy breach. I thought of gathering more information regarding the hosting provider before raising the issue with CERT-MU. To my surprise budgettravel.mu is hosted on the server of a popular ISP of Mauritius, alongwith other websites such the UNDP (un.intnet.mu), Universal ICT Education Programme (uiep.intnet.mu), Mauritius Post (www.mauritiuspost.mu), Mauritius Housing Company Ltd (www.mhc.mu), UoM Insight, Mediacall (mediacall.mu) among several others.
Thus, compromising the server would lead a cyber criminal to potentially compromise all of the above mentioned.
Could the server have been used for a phishing scam?
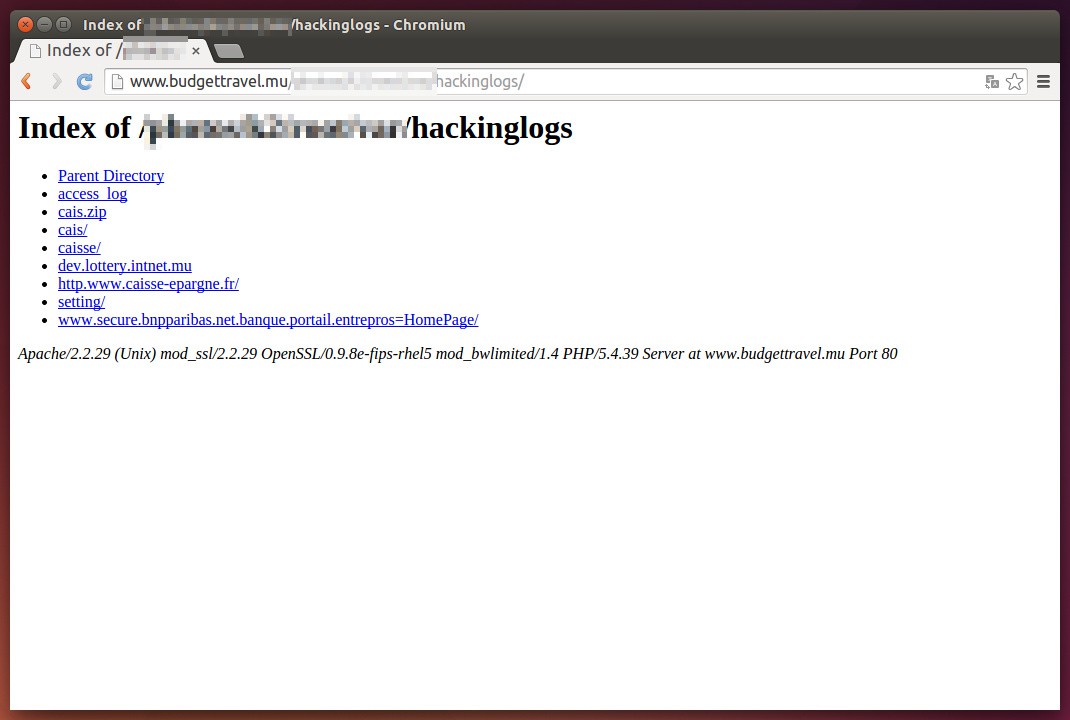
There is one directory named hackinglogs that got me thinking. The list of files/sub-directories is as follows:
I checked the one mentioning BNP Parisbas which is a bank. The directory contains a file named login.php and it reads as follows:
[snipped the javascript tags] echo = "https://www.secure.bnpparibas.net/banque/portail/particulier/HomeConnexion?type=homeconnex&identifiant=secure_bnpparibas_net_20021206152735&navigationId=8a6c8f81edfeaa5683c0d1496711add13bc2de10&ch5=" self.location.replace(echo); window.location = echo;
Clearly, it is a fake login page that would only send the person’s username and password to the attackers Gmail address. I changed the address on purpose. It shows a “possible” phishing scam perpetrated through the ISP’s server.
It’s night, I am tired after a hectic day coding for an SNMP plugin :-) I need rest. As from here I leave it to CERT-MU and Data Protection Office to take over the investigation.