Fighting email forgery with SPF and DKIM
October 28, 2014
Ajay, an experienced fellow from the Linux User Group of Mauritius several times advocated the importance of authenticating emails through SPF and DKIM. Last Saturday, after the Shellshock presentation it was tossed again while Alex and I were discussing a couple of stuffs regarding spams situation and email security. Alex then referred the facility he got with Mandrillapp to sign his emails. I thought, hey wait, this couldn’t be easier, it’s just awesome. Mandrillapp makes DKIM and SPF just a few clicks away. In fact, while he would apply his settings, Ajay did tests instantly to confirm. Yeah, usually DNS changes would take hours to propagate but magic happens with Cloudflare.
 On my end, I looked for a similar facility available with Google Apps. Yup! it’s been now like 2 years since my emails run on Google Apps. I registered at a time when the service was free and I happen to benefit from that.
On my end, I looked for a similar facility available with Google Apps. Yup! it’s been now like 2 years since my emails run on Google Apps. I registered at a time when the service was free and I happen to benefit from that.
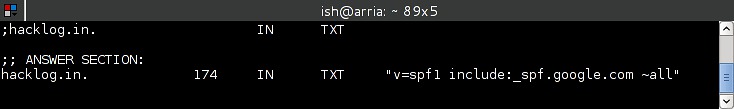
First, let’s configure SPF records to work with Google Apps. It’s pretty easy. One needs only to update the DNS records with a TXT entry as follows v=spf1 include:_spf.google.com ~all. That should be all.
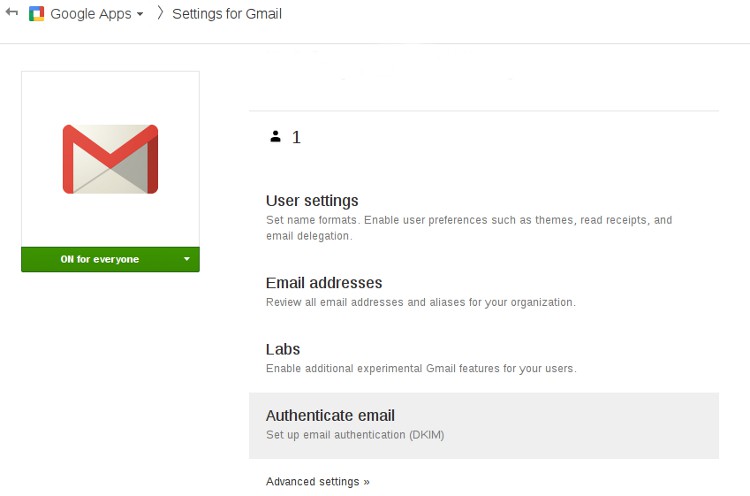
Next, we need to enable DKIM authentication. It starts by generating a domain key for our domain name. With Google Apps this falls under Google Apps > Gmail > Authenticate email from the Google Admin Console.
It will ask for a prefix selector. This can be something that will help in distinguishing different domains. The key will be generated.
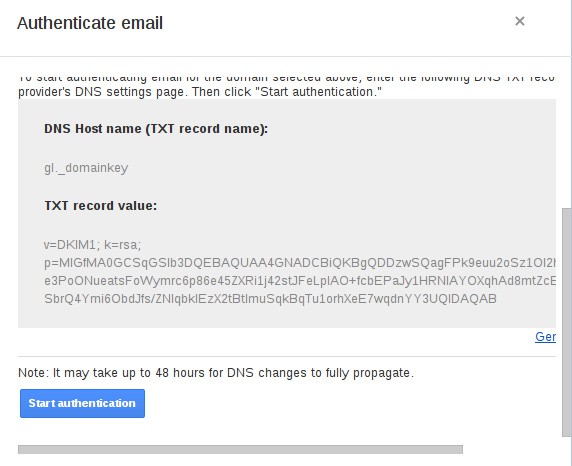
From the above example, we can now add a TXT record with record name as gl._domainkey and record value:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDDzwSQagFPk9euu2oSz1OI2hRHQKoAtk22e3PoONueatsFoWymrc6p86e45ZXRi1j42stJFeLplAO+fcbEPaJy1HRNIAYOXqhAd8mtZcElzGdB2BWlwSbrQ4Ymi6ObdJfs/ZNIqbklEzX2tBtImuSqkBqTu1orhXeE7wqdnYY3UQIDAQAB
Then click Start authentication.
Email headers from legacy.hacklog.in now shows emails as spf=pass and dkim=pass. For testing purposes I sent an email from legacy.hacklog.in to a Hotmail account. Below are header extracts:
SPF and DKIM help your emails gain trust and be delivered to the recipient’s inbox. They also thwart email forgery attempts since those would now fail SPF and DKIM. Forged emails would either be rejected or land in the spam-box.