Coffee at MCB visited by "Hacker Djamel11154"
January 15, 2015
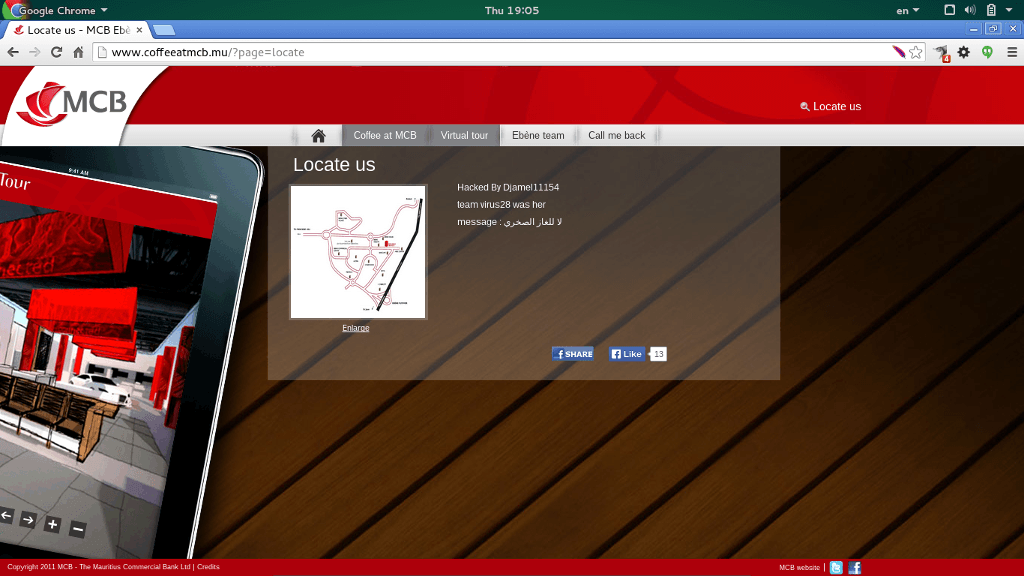
Today I saw an email in the Mauritius Internet Users mailing list that stated there is a problem at www.coffeeatmcb.mu. I visited the website and looked around. Indeed, when I clicked on the “Locate us” link, I find a note left by some “Djamel11154”.
Am I surprised by the above? Nah. Not really.
I noticed another vulnerability linked to this particular website months ago while I had an interview at the same bank. During the interview I notified them about other vulnerabilities lurking on another website that belonged to a subsidiary of the bank. Alas, till today nothing has been done and the vulnerability still lurks on that Linux server ;-)
People might think, Ish, why don’t you just help the bank? Hey, wait, I do write to organizations, be it banks, ISPs, universities or other institutions when I see vulnerabilities in their systems. I don’t publish all of them on my blog. There is no need for that if the admins/webmasters reply promptly and act accordingly. Maybe if Government officials replied promptly in the past too, nothing about those would have been published. It’s only when people guarding data make a deaf ear to security concerns that it becomes important to use other channels.
Now, coming back to the bank, the funny thing is that on the day I had a security presentation (at one of MCB’s subsidiaries) and I had planned to present vulnerabilities & attack scenarios, some so-called very good friend of an infamous project director caused me troubles over Youtube videos where I presented technical aspects of security flaws of the government system. That was a “lol” moment for me though I acted serious. I wonder why people expect me to close my eyes over the wrong.
Anyway, the presentation of vulnerabilities never took place & I wish them good luck in their future endeavors solving their internal/external security flaws. Aww! For info, I am not working for the bank now (^^,) …
For the curious who are worrying about their money at that bank. Chill! The “hacked” website runs on a server which isn’t at the bank premises. The web project must have been outsourced and the web agency either selected a shared hosting service :-) which is another “lol” considering the client is a bank, or the agency could be having one dedicated server but hosts all its customers projects on the same server. Issue with that? Yes. A vulnerability in one of the websites could lead to comprising various others.
Oh! There are other vulnerabilities lurking here and there that could lead to potential sophisticated phishing attacks. When you get emails from this bank, check the domain name under a microscope. I repeat, check the domain name under a microscope!
Update #1
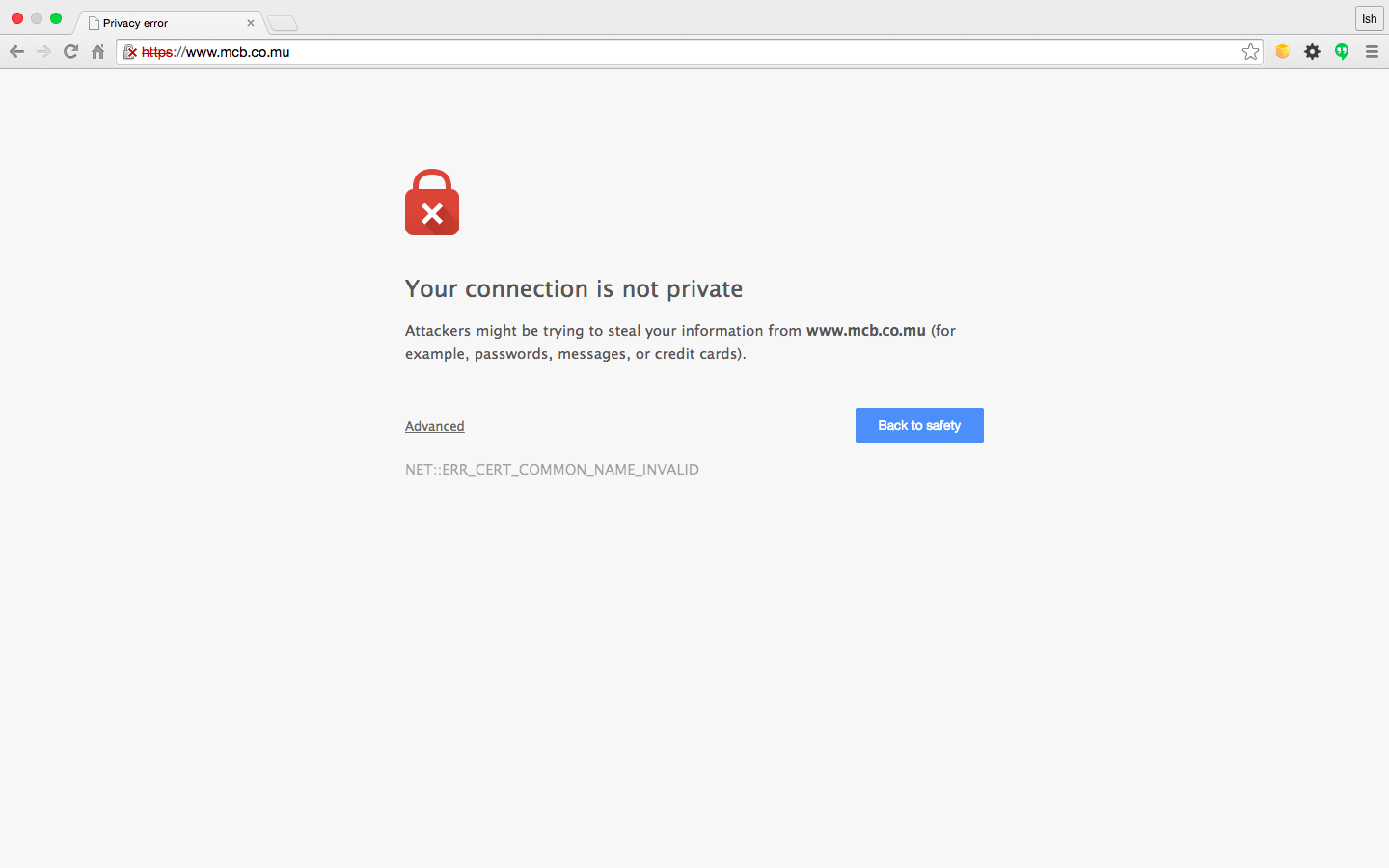
While replying to an email on the Mauritius Internet Users mailing list, I copied the email to alert@mcb.mu, the address as provided by MCB to alert them of security issues. I also notified them of the SSL Certificate error on the MCB website that has been annoying since a long time.
The SSL Certificate error prompts to other ethical issues that won’t be “ethical” to discuss here ;-)
Update #2
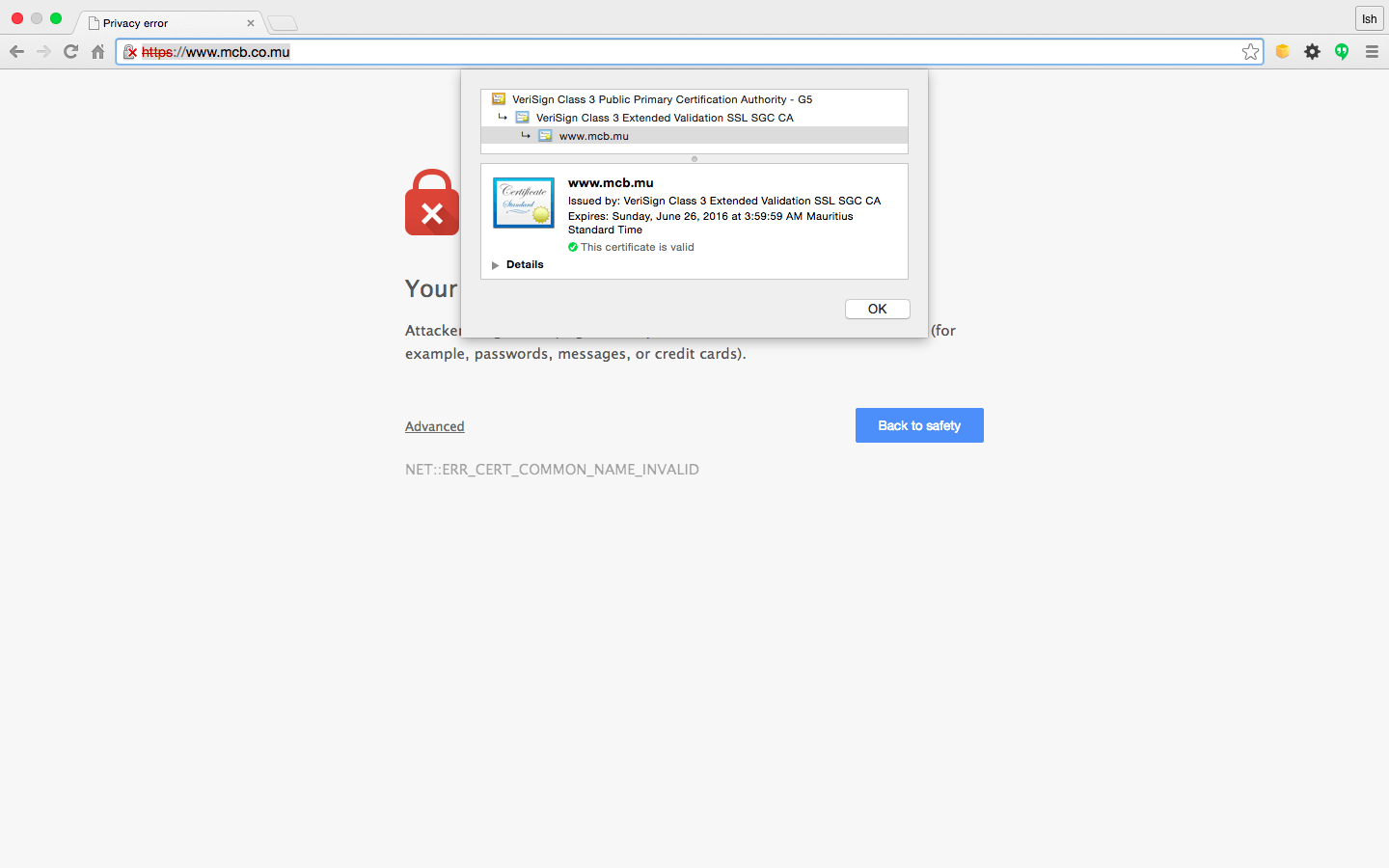
Discussion still going good on the mailing list and this time, I posted another pair of screenshots showing yet another domain of MCB with the wrong SSL Certificate.
Let’s look closely & we might see what’s wrong?
Wrong SSL Certificate ;-) The DNS entries give rise to several questions. The two domain names are managed through different name servers.