ABC Banking Corporation | Phishing mail report
February 26, 2015
While checking my spambox today I noticed a phishing email I received two days ago. Thought of analyzing the stuff, so here we go.
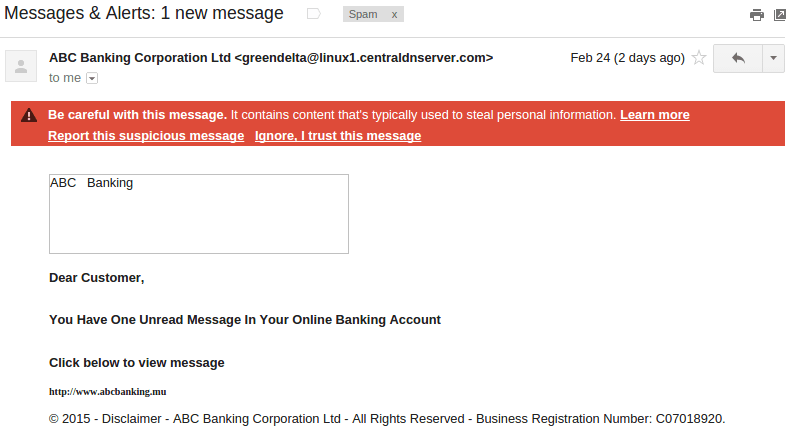
The above is what reached my spam folder. There are enough elements for the email to be tagged as “spam”, however if the attacker was a bit lucky with the server he/she used, it could have landed in my Inbox.
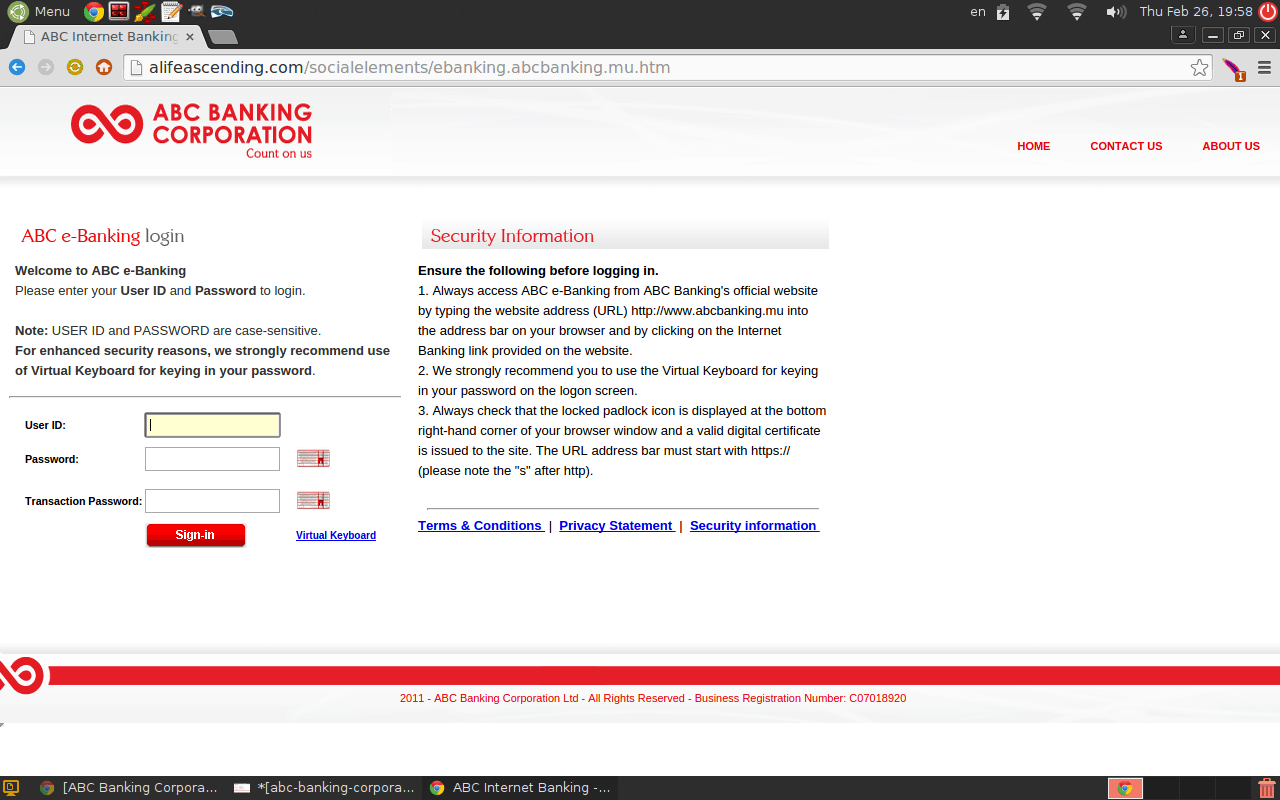
The “customer” is prompted to click on the link http://www.abcbanking.mu to read a message. Upon clicking that, the person would have seen the following page which looks identical to the “login” page of the ABC Banking Corporation.
Notice the URL does not point to abcbanking.mu.
Going through the code of the page I noticed that actual images, JavaScript and CSS elements are loaded from the bank’s URL.
<title>ABC Internet Banking</title>
<link rel="stylesheet" type="text/css" href="https://ebanking.abcbanking.mu/B001/css/abccustom/layout_ib_login.css">
<link rel="stylesheet" type="text/css" href="https://ebanking.abcbanking.mu/B001/css/abccustom/main_layout.css">
<link HREF="https://ebanking.abcbanking.mu/B001/css/cmn/default.css" TYPE="text/css" REL="STYLESHEET">
<script language="JavaScript" type="text/JavaScript" src="https://ebanking.abcbanking.mu/B001/jsdir/virtualkeyboard.js"></script>
<script language="JavaScript" type="text/JavaScript" src='https://ebanking.abcbanking.mu/B001/jsdir/security.js'></script>
<script language="JavaScript" src="https://ebanking.abcbanking.mu/B001/jsdir/common.js"></script>
<script language="JavaScript">
Oh dear! You’re a bank. Please prevent your assets from being hotlinked.
Well, what happens when someone enters login credentials in the form? According to the below code, it’s processed using internet.php which is then surely sent to the attacker.